Secure One Identity Password Manager with OneLogin for Administrators and Help Desk Personnel
SSO & MFA for Helpdesk and Administrators
Recently, I wrote about how you can add Multi-Factor Authentication to your Self-Service Password Resets with One Identity Password Manager and OneLogin.
Read it on the One Identity blog, One Login blog, or my personal blog
In that scenario, a user with a forgotten or expired password authenticates to the self-service portal with a combination of their Security Questions and MFA provided by OneLogin in order to reset their password.
With the release of Password Manager 5.11, we can take this a step further by enabling MFA and/or Single Sign-On for Admins and Helpdesk staff accessing Password Manager using OneLogin, or any other IdP (Identity Provider) that supports standard protocols like SAML (Security Assertion Markup Language).
Introducing Secure Token Server
I'll spare you the details on what this is and keep it simple. rSTS is the same component used in other One Identity products, like Safeguard for Privileged Passwords, to provide federated authentication or multi-step authentication using various providers and protocols like SAML, OAuth, RADIUS, and more. This has now been brought over to Password Manager for use within workflows, and for authentication to the helpdesk and admin web interfaces.
The cybersecurity frameworks, cyber insurance companies, and consulting firms are all correctly on the same page — MFA should be required for access to any privileged application. The admin and helpdesk pages for Password Manager are no exception. Admins can configure the product to do whatever they desire to accounts on all the included domains. Helpdesk staff often have access to unlock or enable accounts, reset passwords, issue BitLocker recovery keys, and more. Enabling MFA as a requirement to access these resources is a logical step towards securing your password reset process.
Options, options...
There are 2 supported methods of configuring federated authentication for the Password Manager Admin and Helpdesk pages, and since I love having options, I'll walk through them both.
External Federation (SSO)
This is a common standards-based scenario where your external Identity Provider of choice acts as the authentication mechanism. This can be both Service-Provider Initiated — where a user navigates to the Password Manager admin or helpdesk portal and gets redirected to the IdP (Identity Provider) for authentication — and Identity-Provider Initiated — where a user signs in to the IdP and clicks an icon on their dashboard to SSO into Password Manager.
Let's use OneLogin as an example. Since it supports SAML2.0, I can create a SAML application called Password Manager, point it to the Password Manager STS (Secure Token Server), and configure Password Manager to use that application for authentication.

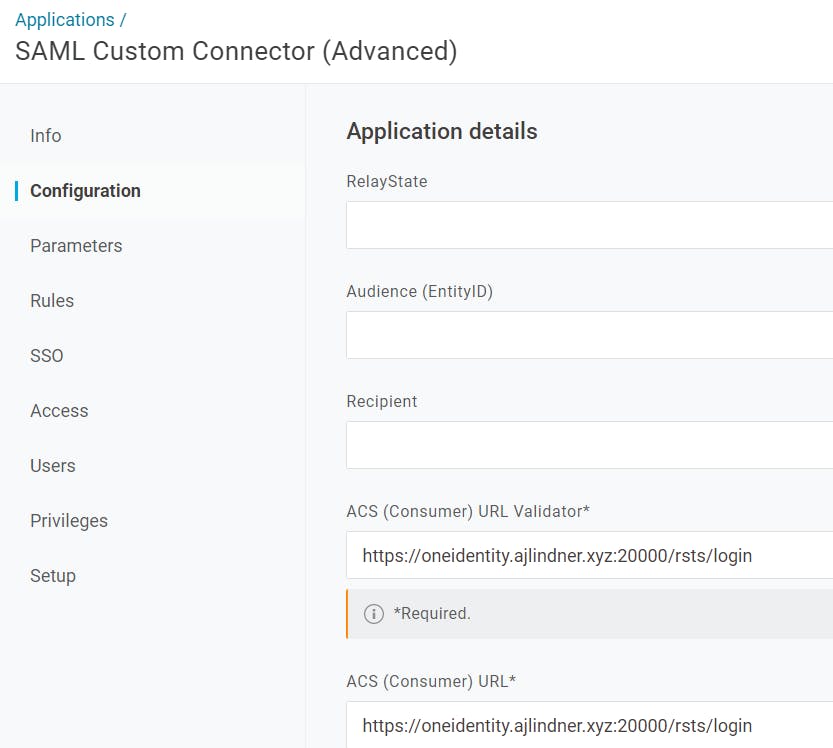
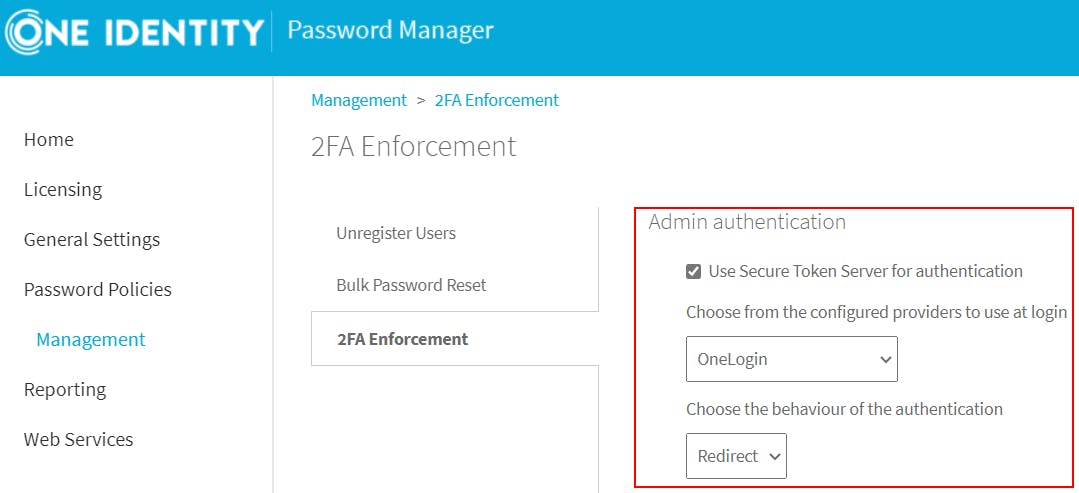
When I access Password Manager's Admin or Helpdesk pages, it will automatically redirect me to authenticate through OneLogin.
But we can take this a step further. OneLogin QuickLinks allow you to create custom applications that show up on the user's SSO Dashboard. These can simply be a URL that the link takes them to, with a custom name and icon to make it easy to identify. So, you can have a single SAML application to handle the authentication, and a QuickLink each for the Admin and Helpdesk pages, that can be assigned to users appropriately.
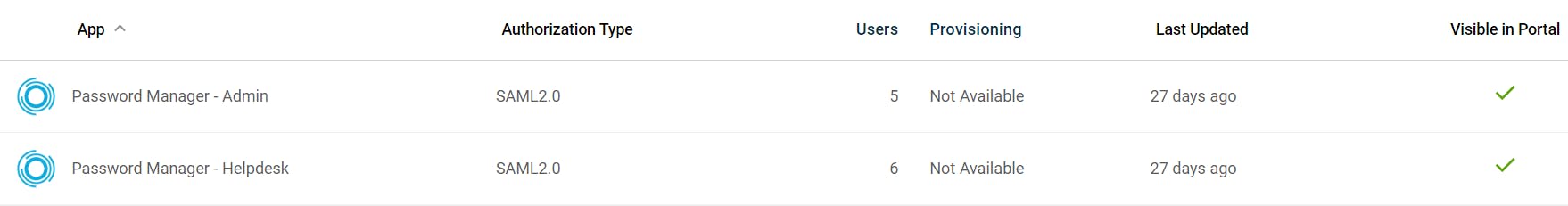
When users sign in to their OneLogin Dashboard, they'll see these links if they are assigned:
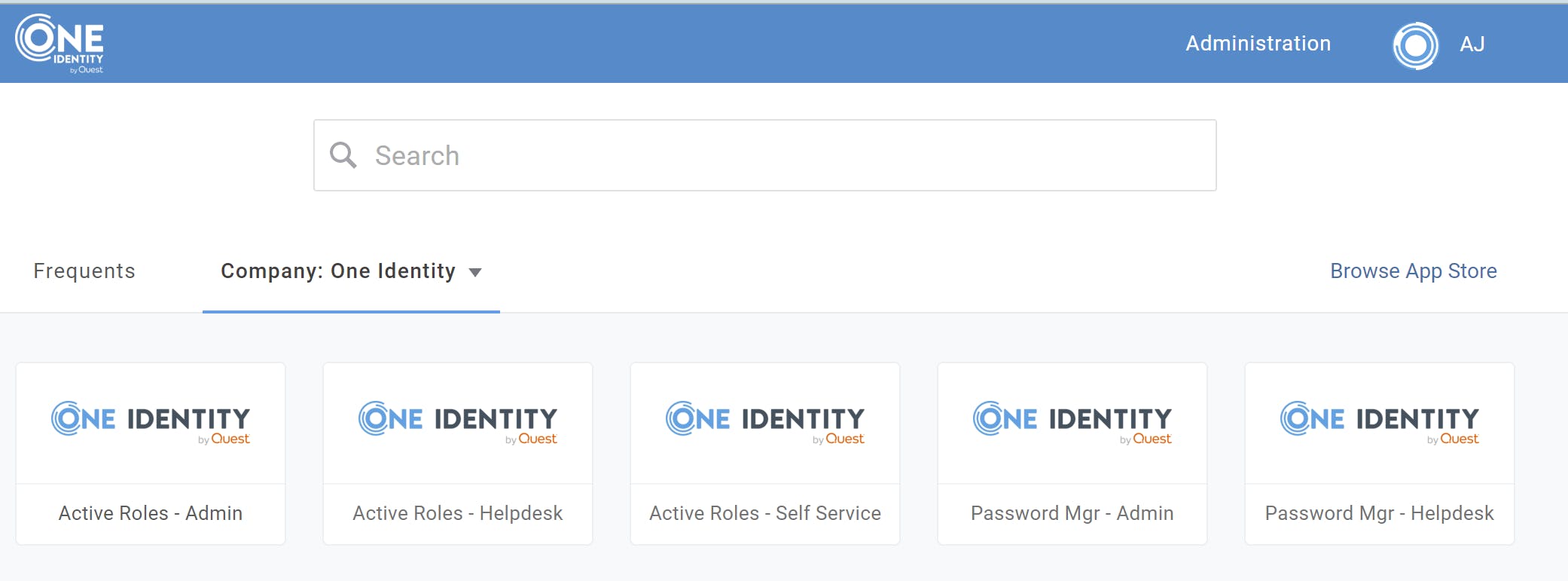
Clicking the link will take them directly to the associated Password Manager URL. And, since they are already authenticated to OneLogin, they'll be automatically signed in.
Right, but what about the MFA?
Of course, the user may already have to authenticate with a second factor when initially signing into their OneLogin dashboard. However, depending on your configuration, this may not be the case. Certain OneLogin Users may have a Security Policy that does not require a second factor when authenticating to their dashboard, or you may be using OneLogin SmartFactor Authentication to suppress the MFA prompt when a low-risk sign-in is detected. In order to ensure MFA is provided when accessing critical applications, regardless of how the user authenticates to their dashboard, OneLogin allows you to create application-specific security policies.
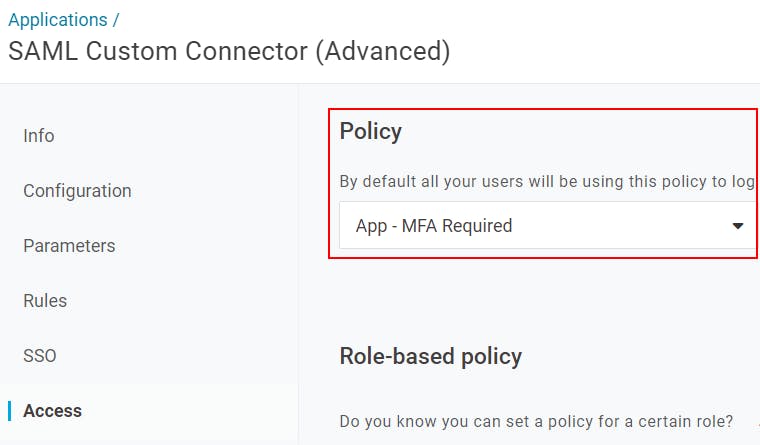
These policies allow you to force an MFA prompt for specific applications, and can of course be configured to suppress that prompt for those users who already provided one in the last X minutes, to avoid multiple prompts in a row.
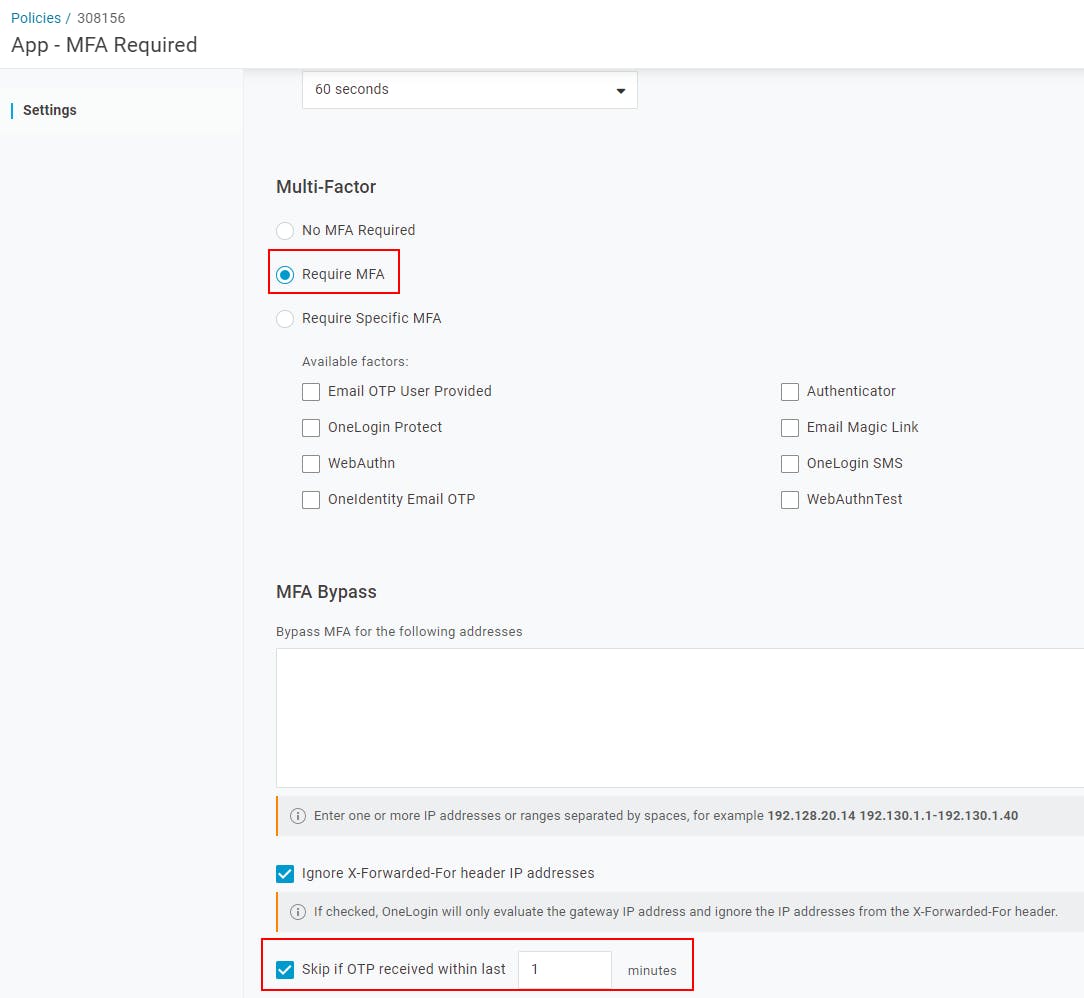
With an Application Security Policy that requires MFA assigned to the Password Manager SAML application, we can ensure that users will always need to provide a second authentication factor in order to access the Password Manager Administration and Helpdesk pages.
What about other IdPs?
Other Identity Providers have their own processes for configuring SAML, OAuth, or WS-Fed authentication, but it's all the same to Password Manager. Even better, it can support multiple Identity Providers for different user groups federating from multiple domains. Keep in mind, however, that this scenario typically expects the Identity Provider to handle both the Primary & Secondary authentication...but it doesn't have to!
Primary Directory Authentication + Secondary Authentication
Our STS allows you to separately configure a primary and secondary authentication method from a choice of standard providers. Want to still have AD (Active Directory) Authentication but use a RADIUS server for MFA? No problem! How about LDAP (Lightweight Directory Access Protocol) & Duo? That works too.
This scenario is more flexible for organizations who are not standardized to an IdP across the board or have existing standalone MFA solutions that only provide secondary authentication and rely on a primary authentication source like Active Directory.
Summary
Whether you're fully committed to the latest and greatest of security frameworks, fighting an uphill battle to implement any security controls you can, or balancing security and usability concerns anywhere in between, One Identity Password Manager offers configuration and extensibility options to help you design a secure password reset process that adheres to your unique requirements, without compromising the experience for your end users.
Requiring MFA for the privileged Admins and Helpdesk Users accessing Password Manager, and for the end users performing password resets, is one of the easiest first steps you can take towards securing the entire process.
External Links
Read the first post in the series on Secure Password Resets with One Identity Password Manager:
View this article elsewhere:
